Sysmon 101

Introduction to Sysmon
I decided to write this article about Sysmon after my struggle to find any basic Sysmon 101 article. Although there are plenty of articles explaining how to install sysmon, I never found any good article on how sysmon rules work together. After some error and trials I was finally able to figure it out.
Log and monitoring is considered an important security control to protect your IT environment. Logging is the first step for an effective monitoring program. However what and how much to log? is still something that SOC (Security operations centre) engineers grapple with everyday. This coupled with annual security compliance requirements have made the job of SOC engineers very difficult. Moreover it has crippled SOC’s to implement an effective security monitoring program.
Recently, I had the oppurtunity to attend Eric conrads talk at Atlantic Security conference in Halifax. Eric mentioned something very interesting about having a compliance SIEM and strategic SIEM. Sysmon is considered to be an awesome tool for capturing what is considered to be “relevant” events and something that can feed our strategic SIEM. I wont be explaining how to install Sysmon here but if you are new to Sysmon I would highly recommend reading official Microsoft documentation
However there are two commands that can get you up and running quickly
sysmon -accepteula –I (This would install sysmon)
sysmon –c <PATH TO CONFIG> (Config File to use)
In order to effectively use Sysmon one has to define what events to capture from a Windows system. This is done by using the configuration file for Sysmon. This configuration is an XML file which contain the “Rules” to capture or discard certain events. The XML configuration file for Sysmon has a particular format, you can get more information from the official documentation. However for each event category one need to define filters.
Filters can be explained by taking an example, lets say you want to capture event for launching cmd.exe, how would you define the filter? Well first since its a process creation event we will define the filter under ProcessCreate Tag. Following is the resulting config file to capture the event for cmd.exe.
<Sysmon schemaversion=”10.4">
<HashAlgorithms>md5,sha256</HashAlgorithms>
<CheckRevocation/>
<EventFiltering>
<ProcessCreate onmatch=”include”>
<Image condition=”contains”>cmd.exe</Image>
</ProcessCreate>
</EventFiltering>
</Sysmon>
Here is the breakdown of this simple configuration file.
Sysmon Tag: Used to tell sysmon begining of configuration file along with version of Sysmon running on your system.
Hash Algorithm Tag: Used to specify the hash algorithms, these algorithms are used to identify files.
Event Filtering Tag: Used to contain the different Sysmon event categories.
ProcessCreate tag: Used to tell Sysmon that we are going to start defining filters for the first category of Sysmon event. This category is used to capture events as they relate to process creation. You will also notice we have “onmatch=”include” ” which is telling Sysmon to include the events which match the filters specified beneath this tag. Sysmon will capture all the events matching the filters and discard everything else, the opposite will be true if we had onmatch set to “exclude”.
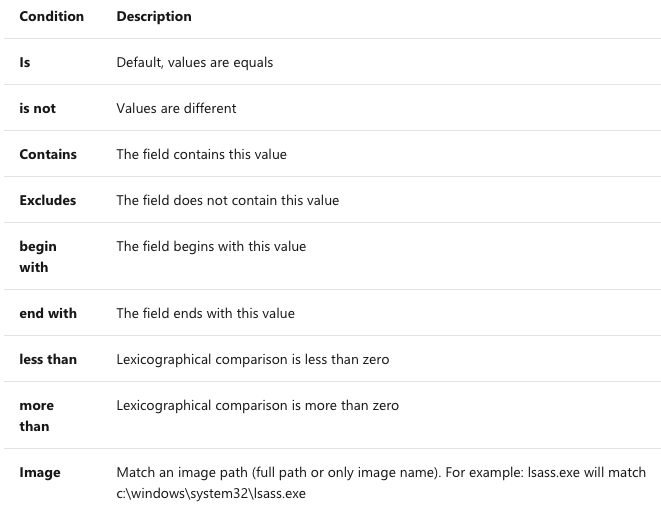
Image tag: This is our filter. Dont be confused by Image it it just another name to specify compiled binary. Now we need to discuss a little more about condition but they are just used to match a condition. The table below provide more information
Lets take another example this time we want to capture network events. Here is a basic Sysmon configuration file to capture network events for port 80, 443 and 22. Here is what the config file would look like.
<Sysmon schemaversion=”10.4">
<HashAlgorithms>md5,sha256</HashAlgorithms>
<EventFiltering>
<NetworkConnect onmatch=”include”>
<DestinationPort condition=”is”>443</DestinationPort>
<DestinationPort condition=”is”>80</DestinationPort>
<DestinationPort condition=”is”>22</DestinationPort>
</NetworkConnect>
</EventFiltering>
</Sysmon>
Now lets test this, I can open my browser for testing but I will use PowerShell to test.
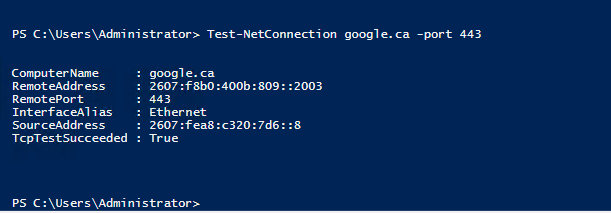
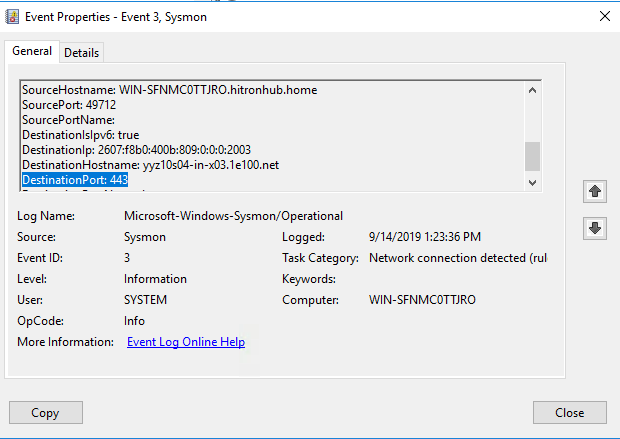
Now this was easy, but what if we want to filter based on Destination IP? Well we can and its simple, all i need to do is add following to my configuration file
<DestinationIp condition=“is”>8.8.8.8</DestinationIp>
BUT here is a GOTCHA!!! First, Here is what my filters look like in my configuration file.
<NetworkConnect onmatch=”include”>
<DestinationIp condition=”is”>8.8.8.8</DestinationIp>
<DestinationPort condition=”contains”>80</DestinationPort>
<DestinationPort condition=”contains”>443</DestinationPort>
<DestinationPort condition=“contains”>53</DestinationPort>
</NetworkConnect>
But when I use this file I will only see logs if the “DestinationIp” is 8.8.8.8 AND “DestionationPort” is 80 OR 443 OR 53. Any other destination IP and I wont see any events being generated. Let’s make it more interesting what if I have following in my Config.xml file
<NetworkConnect onmatch=”include”>
<Image condition=”contains”>chrome.exe</Image>
<Image condition=”contains”>svchost.exe</Image>
<Image condition=”contains”>powershell</Image>
<DestinationIp condition=”is”>8.8.8.8</DestinationIp>
<DestinationPort condition=”contains”>80</DestinationPort>
<DestinationPort condition=”contains”>443</DestinationPort>
<DestinationPort condition=“contains”>53</DestinationPort>
</NetworkConnect>
Well this means that I will only see log entries if: “Image/Process” contains chrome.exe OR svchost.exe OR powershell AND “Destination IP” is 8.8.8.8 AND “Destination Port” is 80 OR 443 OR 53.
So it means that if you are filtering on same condition its the OR switch but if you keep adding filter it’s AND condition. I banged my head against the computer for 2 hours before I figured this out.
I hope this atricle would have helped you to understand how Sysmon rules works. If you want to learn more about Sysmon here is a list of few resources
Sources:
https://github.com/SwiftOnSecurity/sysmon-config
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
https://cqureacademy.com/blog/server-monitoring/sysmon
https://posts.specterops.io/working-with-sysmon-configurations-like-a-pro-through-better-tooling-be7ad7f99a47
https://www.darkoperator.com/blog/2014/8/8/sysinternals-sysmon